9 A.M Monday, and you have reported to work. At your desk you enter your password expecting to start the week's work. You may be an appointment clerk or a back offfice nurse.
The physician is not at the office as yet. He is unaware of the pending disaster and interruption to patient care.
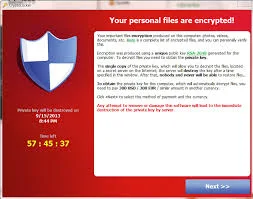
You enter your password and 'enter'. The screen hesitates a bit longer and a screen pops up. You are a bit disoriented since it is Monday morning and you have never seen this screen before.
It may be any one of these screenshots, taken from real victims of this nefarious scheme of cybercriminals. They have a variety of names, and all are known as Ransomware.
Different Types of Ransomware
CryptoLocker
CryptoLocker botnet is one of the oldest forms of cyberattacks that have been around for the past two decades. The CryptoLocker ransomware came into existence in 2013 when hackers used the original CryptoLocker botnet approach in ransomware. CryptoLocker is the most destructive form of ransomware since it uses strong encryption algorithms. It is often impossible to decrypt (restore) the Crypto ransomware-infected computer and files without paying the ransom.
WannaCry
WannaCry is the most widely known ransomware variant across the globe. The WannaCry has infected nearly 125,000 organizations in over 150 countries. Some of the alternative names given to the WannaCry ransomware are WCry or WanaCrypt0r.
Bad Rabbit
Bad Rabbit is another strain of Ransomware which has infected organizations across Russia and Eastern Europe. It usually spreads through a fake Adobe Flash update on compromised websites.
Cerber
Cerber is another ransomware variant that targets cloud-based Office 365 users. Millions of Office 365 users have fallen prey to an elaborate phishing campaign carried out by the Cerber ransomware.
Crysis
Crysis is a special type of ransomware that encrypts files on fixed drives, removable drives, and network drives. It spreads through malicious email attachments with double-file extension. It uses strong encryption algorithms making it difficult to decrypt within a fair amount of time.
CryptoWall
CryptoWall is an advanced form of CryptoLocker ransomware. It came into existence since early 2014 after the downfall of the original CryptoLocker variant. Today, there are multiple variants of CryptoWall in existence. It includes CryptoDefense, CryptoBit, CryptoWall 2.0, and CryptoWall 3.0.
GoldenEye
GoldenEye is similar to the infamous Petya ransomware. It spreads through a massive social engineering campaign that targets human resources departments. When a user downloads a GoldenEye-infected file, it silently launches a macro which encrypts files on the victim's computer.
Jigsaw
Jigsaw is one of the most destructive types of ransomware which encrypts and progressively deletes the encrypted files until a ransom is paid. It starts deleting the files one after the other on an hourly basis until the 72-hour mark- when all the remaining files are deleted.
Locky
Locky is another ransomware variant that is designed to lock the victim's computer and prevent them from using it until a ransom is paid. It usually spread through a seemingly benign email message disguised as an invoice.
When a user opens the email attachment, the invoice gets deleted automatically, and the victim is directed to enable macros to read the document. When the victim enables macros, Locky begins encrypting multiple file types using AES encryption.
Apart from the list of attacks mentioned above, Petya, NotPetya, TeslaCrypt, TorrentLocker, ZCryptor, etc., are some of the other ransomware variants that are well-known for their malicious activities. Some of these ransomware malware are focused on gaming sites, not on healthcare centers. TeslaCrypt is now defunct
Fortunately, a whole new industry devoted to recovering encrypted data from ransomware has evolved. The Federal Bureau of Investigation now has a cybersecurity division led by ex-hackers, and who cooperate for a plea bargain.
The effect is that.you computer has been encrypted and the demand for payment includes a deadline after which your data will be permanently deleted. This allows you time to make a.decision to comply and pay. The amount demanded is considerable and depends upon the organization that has been attacked.
Now that we have introduced you to the worst day of your work life you will need a process ready in place. That at least will give focus on the next steps.
1. You should already have a crypto-insurance policy. They are available and worth the expense. Attacks are not rare anymore. In fact, ransomware has evolved. Many of the original ransomware (WannaCry) is passe, having been used enough that cybersecurity experts have decoded them. Payments are usually demanded in some form of cryptocurrency which cannot be traced.
The 10 Best Cyber Insurance Providers for 2020
No need to list them here, just go to the link
We have all read about ransomware intrusions into large enterprise systems: The financial reward is much greater since enterprise systems will more likely pay the ransom, in lieu of decrypting their databases which can be very large.
The University of Utah pays $457,000 to ransomware gang | ZDNet
The University of Utah pays $457,000 to ransomware gang | ZDNet






Very Informative Blog. Thanks For updating. Here is Rileys Spice.
ReplyDeleteRiley’s Spice of Life Salsa seasoning is great in any type of Mexican style foods like taco meat, burritos, and fajita. It can be used in soups, dips, meatloaf, and hamburgers. Try it in dishes like prawns and hot butter, corn on the cobb and hash-browns & scrambled eggs. Check out our recipes on this website and then share your recipes with us!
https://rileyspice.com/